Lorsque vous utilisez VIPN, vous vous connectez à SNO et vos données circulent sous forme de flocons mélangés aux autres. Vous êtes invisible.
En quelques mots
Le paradigme actuel de la cybersécurité — la confiance — a atteint ses limites : avec l’omniprésence des technologies de l’information et de la communication (TIC), la complexité croissante des chaînes d’approvisionnement numériques et l’essor mondial du marchés des vulnérabilités et exploits, les CVE se sont multipliées au cours des dix dernières années et rendent les chaînes de confiance de moins en moins pertinentes.
La technologie VIPN a donc été conçue pour qu’ aucun utilisateur n’ait besoin de faire confiance à ses composants. Nous y parvenons en rendant les utilisateurs, les équipements et les données invisibles sur Internet : même en présence d’une vulnérabilité sur la chaîne de confiance, celle-ci ne doit pas être exploitable par des observateurs, qu’il s’agisse de script kiddies ou d’acteurs étatiques.
Ainsi, les utilisateurs deviennent indépendants de l’infrastructure sous-jacente au sens large du terme (c’est-à-dire les logiciels, le matériel, les couches cryptographiques et, bien entendu, Snowpack).
VIPN: Virtual & Invisible Private Network
VIPN propose une approche radicalement différente des modèles de menace en :
1/. empêchant l’identification et l’analyse du trafic en « supprimant » données et métadonnées (e.g. adresses IP, protocoles), et non en les dissimulant simplement sous une ou plusieurs couches de chiffrement, afin d’éviter l’interception, l’analyse DPI (Deep Packet Inspection) et les perturbations ciblées sur les backbones ;
2/. dissimulant les endpoints en permettant aux serveurs d’opérer sans ouvrir de port d’écoute.
Cette approche s’appuie sur un principe classique : le routage d’informations complémentaires fragmentées à travers des chemins disjoints, au moyen d’un mécanisme de partage de secret. L’accès cleartext nécessite donc l’identification de l’ensemble des fragments complémentaires : il est en effet impossible de reconstituer l’information d’origine en interceptant un seul fragment (ou même n-1 fragments).
Au cours des années 2000, de nombreux travaux de recherche ont exploré cette idée. Cependant, comme ils s’appuyaient sur les protocoles IP standards, l’identification des fragments complémentaires restait relativement aisée grâce à l’analyse des métadonnées sur le backbone (e.g. adresses IP). VIPN introduit une innovation supplémentaire en anonymisant ces fragments — que nous appelons « flocons » — et en les routant via des circuits construits de manière anonyme. Ce point constitue l’une des deux clés des propriétés de VIPN et repose sur un mécanisme d’auto-découverte basé aussi sur les flocons, décrit dans le premier brevet ainsi que dans notre livre blanc.
Ainsi, un attaquant utilisant des techniques d’interception « industrielles » sur le backbone peut avoir une forte probabilité d’« observer » les flocons complémentaires. Mais, comme ceux-ci sont anonymes et indiscernables les uns des autres (taille identique, contenu non intelligible), l’attaquant devrait enregistrer l’intégralité du trafic réseau puis effectuer une attaque par force brute sur la surcouche — c’est-à-dire tester toutes les combinaisons possibles de flocons afin d’identifier les fragments complémentaires et de reconstituer les paquets IP, une opération dont la complexité suit une loi de puissance qui dépend du nombre de flocons.
Même si une telle attaque était réalisable, l’attaquant n’obtiendrait in fine que des paquets IP anonymes et devrait encore inspecter le contenu de chacun d’eux pour tenter d’y déceler des indices de désanonymisation.
Architecture et grands principes
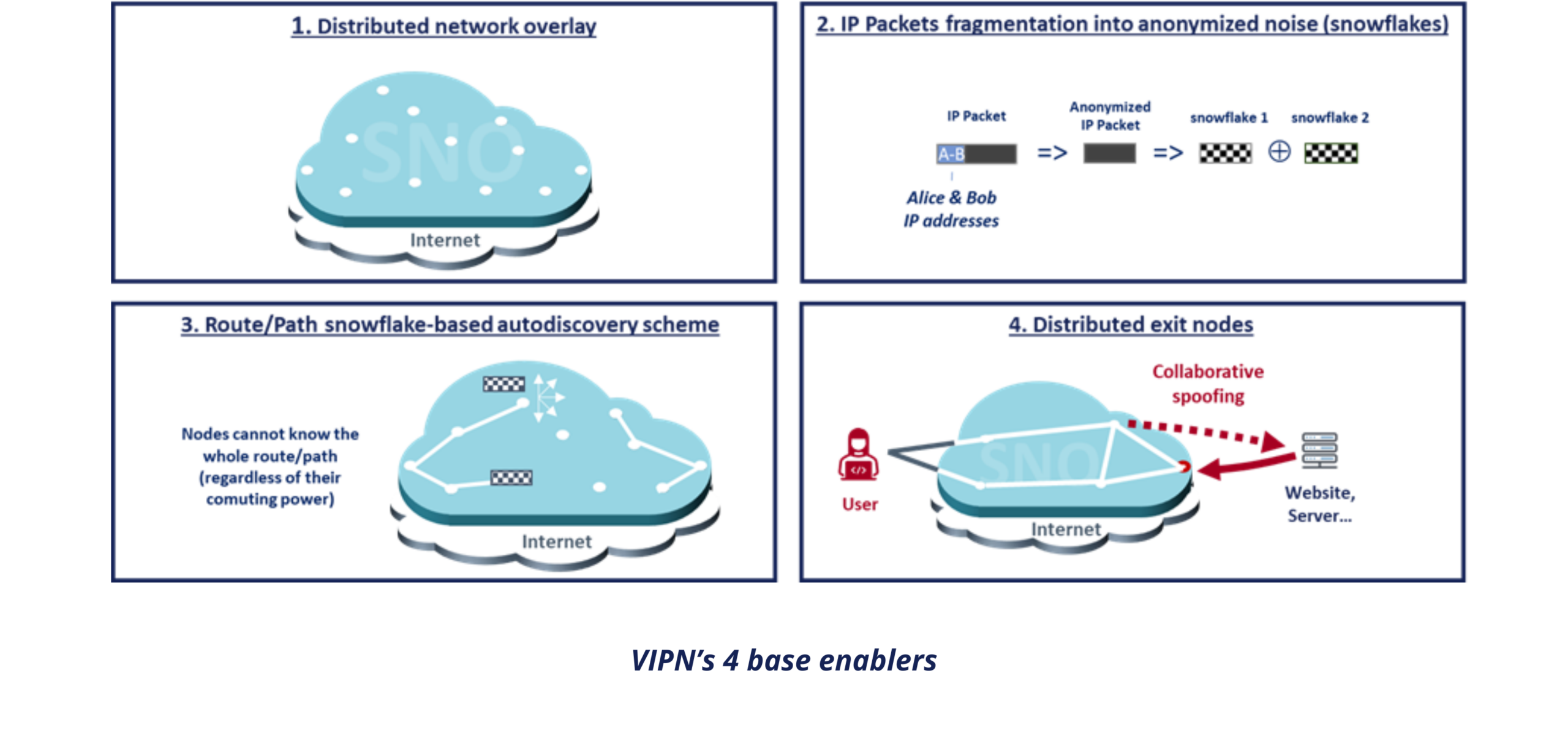
VIPN repose sur la combinaison de quatre « feintes » complémentaires :
- Une architecture basée sur réseau overlay (SNO), opéré par Snowpack, ses partenaires et certains clients, que l’utilisateur accède via un connecteur installé sur un device ou une passerelle ;
- La fragmentation de paquets IP anonymisés en « flocons » au moyen d’un mécanisme de partage de secret (actuellement basé sur l’opérateur logique XOR), utilisé à la fois pour la création des routes et pour le transfert de données ;
- Un mécanisme d’auto-découverte fondé sur les flocons, garantissant la création de routes anonymes aussi bien en mode « Privacy » qu’en mode « Tunnel » ;
- Une distribution des nœuds de sortie reposant sur un spoofing collaboratif entre deux nœuds SNO sélectionnés par l’utilisateur, afin de prévenir toute attaque de type homme-du-milieu (MITM) lors de la création des routes en modes « Privacy » et « Tunnel».
Ces principes fondamentaux sont décrits dans le brevet fondateur, ainsi que dans notre livre blanc (qui inclut également le modèle de menace associé). Ils ont par ailleurs été largement diffusés en France à travers des podcasts spécialisés en cybersécurité (par exemple OSSIR et NoLimitSecu) ainsi que lors de la conférence C&ESAR 2025.
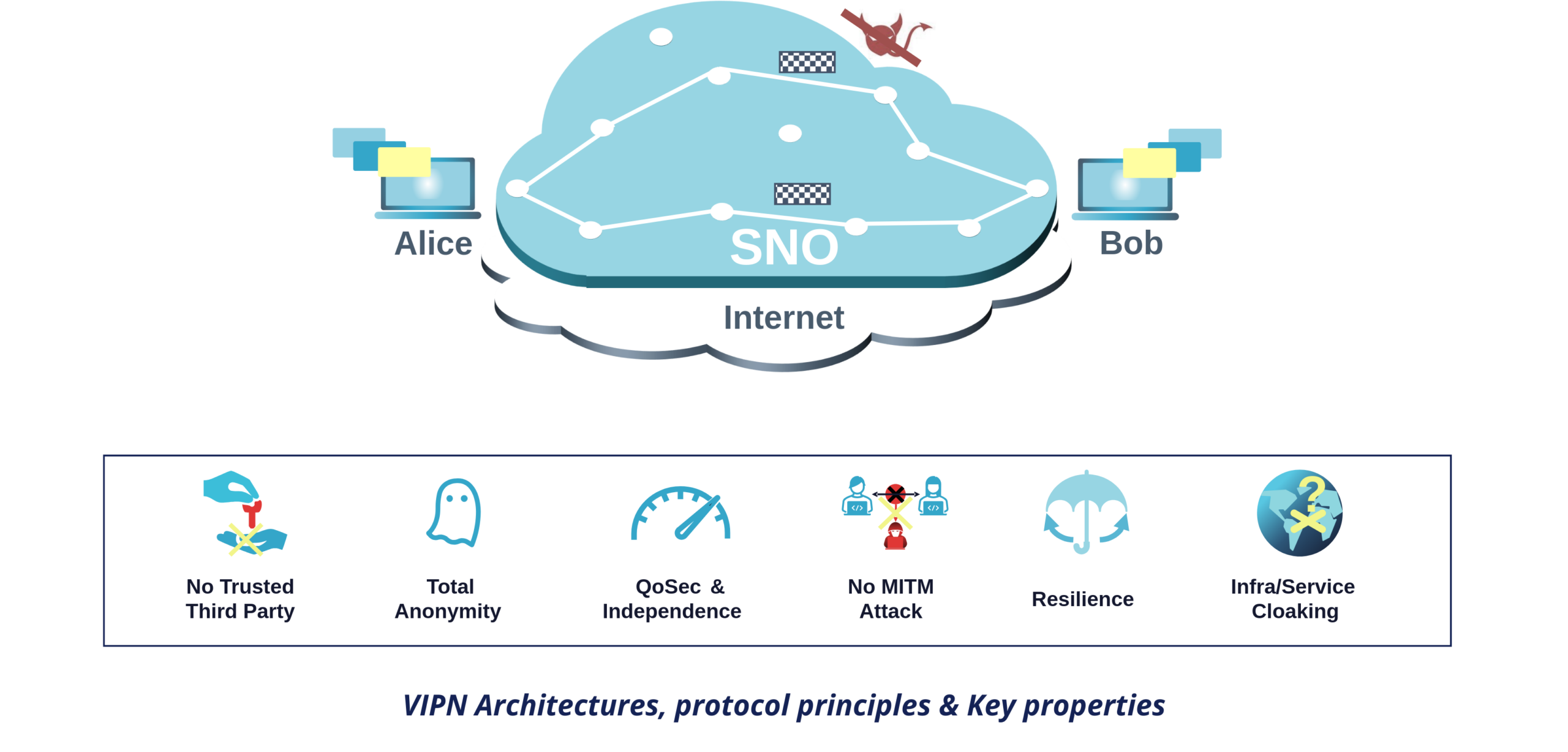
Propriétés principales
Comme VIPN ne repose pas uniquement sur le chiffrement TLS standard entre nœuds, mais également sur des flocons transmis via des routes construites de manière anonyme, les utilisateurs n’ont pas à faire confiance aux nœuds. Indépendamment de leur capacité de calcul, aucun nœud n’est en effet en mesure de connaître l’origine, la destination ou le contenu d’un flocon, puisqu’il n’a jamais accès à ces éléments — pas même sous forme chiffrée.
Cette approche confère plusieurs propriétés complémentaires :
- Résilience : les nœuds sont hébergés chez de multiples hébergeurs et fournisseurs et opérés par différents partenaires ;
- Absence de tiers de confiance et anonymat réel : ni Snowpack, ni ses partenaires, ni ses clients ne peuvent identifier une route. Ils sont donc dans l’incapacité de rompre l’anonymat et l’invisibilité des communications ;
- Qualité de sécurité (QoSec) : par conception, les trafics utilisateurs sont indiscernables, y compris au niveau des métadonnées, lesquelles sont encapsulées dans les flocons. Toute attaque ciblant les communications sur SNO nécessite donc une attaque par force brute de l’intégralité de l’overlay. Ceci requière au préalable le déploiement de sondes sur l’ensemble des nœuds SNO (ou entre les nœuds) et l’enregistrement du trafic complet pour collecter tous les flocons. Cette étape est, en pratique, irréalisable, y compris pour un État-nation. Et quand bien même elle le serait, l’attaquant devrait ensuite tester toutes les combinaisons de flocons, une opération dont la puissance de calcul requise croît selon une loi de puissance du nombre de flocons. Cette puissance peut être estimée à partir des données fournies par SNO et contrôlée grâce à des « canons à neige » injectant des flocons supplémentaires (générés naturellement par le trafic des utilisateurs gratuits ou artificiellement par Snowpack) ;
- Immunité aux attaques de type homme-du-milieu (MITM) : par conception, les attaques MITM, qui constituent le socle des attaques réseau, sont impossibles ;
- Dissimulation de la surface d’attaque : grâce à une architecture inspirée de Tor, adaptée à nos protocoles, les serveurs protégés par VIPN peuvent être accessibles sans connaissance de leurs adresses IP, sans recours à un tiers de confiance, et fonctionner sans aucun port d’écoute ouvert
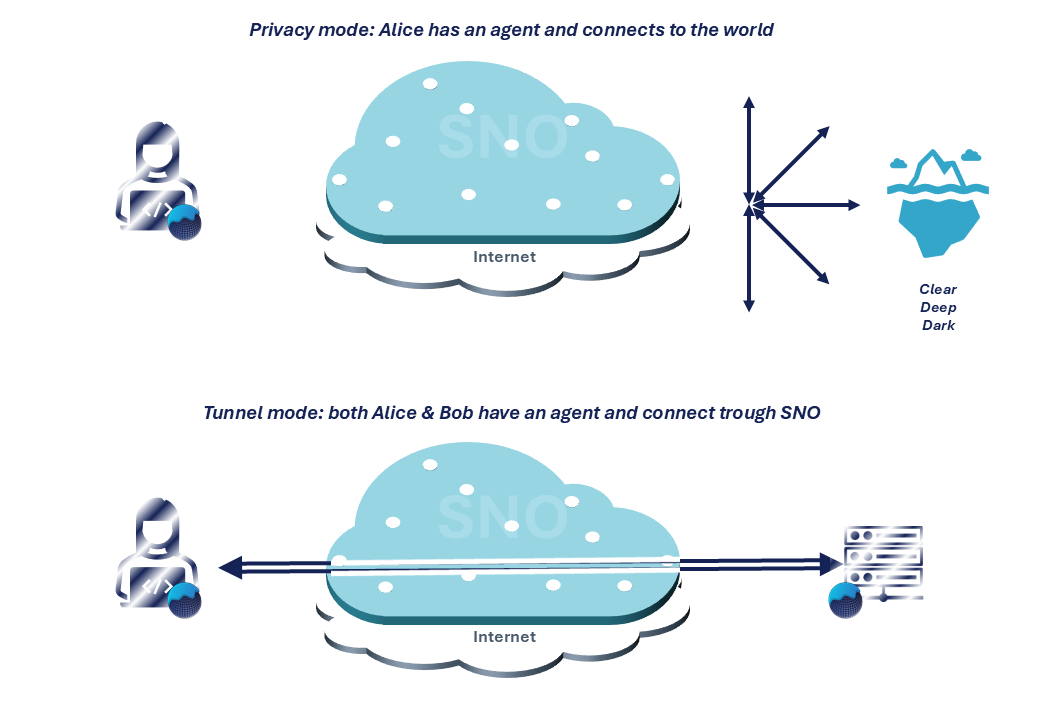
Les 2 modes VIPN actuels
À l’instar de Tor (accès au clearnet et aux services Onion) et des VPN (VPN grand public ou VPN site-à-site), VIPN propose deux modes de fonctionnement :
- Mode « Privacy » (non collaboratif) : ce mode s’apparente à un proxy ou à un service de VPN grand public. Dans ce cas, seule Alice doit disposer d’un agent VIPN. Cet agent dissimule l’identité d’Alice via SNO, en lui fournissant un point d’entrée temporaire vers le Clear Web, le Deep Web et le Dark Web. Pour l’accès aux sites en .onion, ce mode peut être intégré de manière transparente avec Tor ;
- Mode « Tunnel » (collaboratif) : ce mode se rapproche d’une connexion VPN site-à-site ou d’un accès distant sécurisé. Alice et Bob disposent tous deux d’un agent VIPN afin de construire une route sur SNO. En pratique, la création du tunnel s’inspire de l’architecture des services Onion et s’appuie sur le mode « Privacy » afin de garantir les propriétés uniques du tunnel
blanc