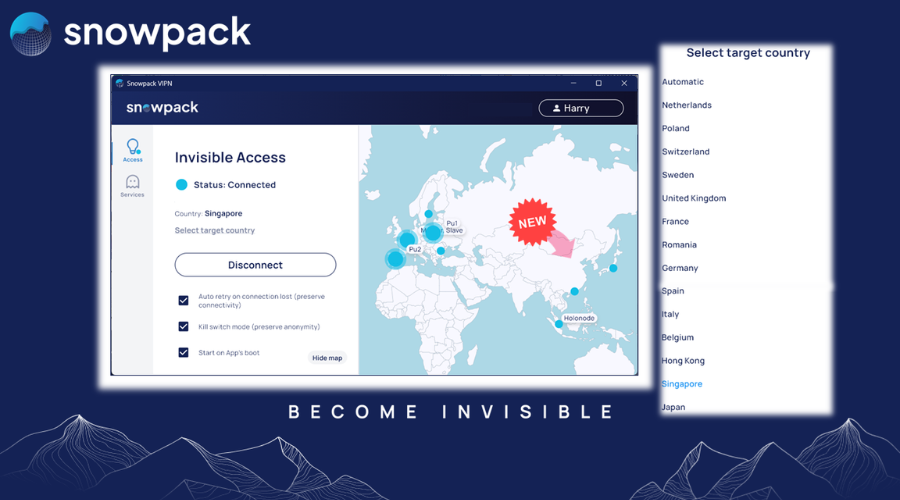
Turnkey solution to make your sensitive web services invisible from hackers.
Cloak your endpoints & data-in-transit from hackers and prevent vulnerabilities & traces exploitation.
- Remote working and mobility
- Cloud & Remote Security
- OpSec for OSINT & digital investigation
- Anonymized threat intelligence sharing
-
Protect yourself anywhere and be as safe at work as at homeRequest a demo More information
Whether you’re traveling , at work, or at home, we guarantee the same level of security and privacy everywhere.
Thus, protect your know-how and your identity.
-
Secure your Entire External Attack SurfaceRequest a demo More information
Is your information system split between your main site, various secondary sites and even cloud instances? Your collaborators are working from anywhere ?
Connect all these elements together easily and without exposing open ports, thanks to the unique properties of our VIPN technology.
-
Operational security of open-source intelligence gatheringRequest a demo More information
Protect yourself from information bubbles and attribution risks in your open source researches and online activities.
Take advantage of our advanced solutions to conduct online research with a high level of privacy and securely access your digital identities.
Ability to use different IP addresses to isolate your searches and preserve the privacy of your online activities.
Flexible choice of exit points to suit your operational needs.
Automated definition of your routes, according to your privacy requirements.
Simplified integration with your monitoring tools (SIEM, proxy servers.
-
Share security alerts and IoCs with other organizations in your industry without revealing your identity.Request a demo More information
Collectively protect your ecosystem by reporting detected threats, while maintaining your organization’s confidentiality.
Report detected vulnerabilities and threats without revealing that your organization has been affected.
Cryptographic authentication ensures that the intel comes from a verified member of the group (previously established).
Certified integrity: other members can verify authenticity without knowing the source.
Organizations receive real-time alerts to prevent similar attacks on their own organizations.
GDPR compliance: no personal data is shared, only technical indicators.
Collective learning: mutual improvement of the sector’s security posture.