Our VIPN connects to SNO, transforming your data into snowflakes and melting them into the snowpack, so that you become invisible.
in a nutshell
Snowpack’s patented VIPN technology has been developed with the idea that the present cybersecurity paradigm, Trust, as reached its limit. With ICT pervasiveness, , the increasing complexity of ICT supply chains, and the thriving worldwide vulnerabilities and exploits market, CVE have expanded during the past decade making the chain of trusts less and less relevant. This is why, VIPN was designed with a “Beyond Trust” by-design approach: no user should have to trust any element of the network overlay. We achieved that by making users, devices and data invisible on Internet: even if there is a vulnerability somewhere in the chain of trust, it should not be exploitable by observers, whether script-kiddy or nation-state. As a result, users become independent from the underlaying infrastructure in the broader sense of the term (i.e., software, hardware, cryptographic layers and of course Snowpack).
VIPN: Virtual & Invisible Private Network
VIPN offers a radically different approach to network security threat models by:
1/. Preventing traffic identification and analysis by “removing” data and metadata (e.g. IP addresses, protocol) and not just hiding these under encryption layer(s) to prevent sniffing and targeted disruptions on Internet backbones through Deep Packet Inspection appliances;
2/. Cloaking endpoints by removing the necessity for servers to operate with open listening ports.
This is achieved by building over a classic approach: routing complementary fragmented information through disjoint paths using a secret-sharing mechanism. Accessing cleartext therefore requires identifying all complementary fragments: it is indeed impossible to find out the original information by intercepting just one fragment (or n-1 fragments). Throughout years 2000s, research papers explored this idea but relied on standard IP protocols and identification of complementary fragments remained easy thanks to metadata analysis on backbones (e.g. IP addresses). VIPN introduces a new trick by anonymizing these fragments (we call them “snowflakes”) and routing them through anonymously built circuits. This last point is one of the two keys to VIPN’s properties and is achieved through a snowflake-based auto-discovery mechanism described in the first patent and in our whitepaper.
As a result, an attacker using “industrial” interception techniques on backbones may have a high probability of “seeing” the complementary snowflakes, but as all snowflakes are anonymous and look-alike (same size, no intelligible content), the attacker needs to record the whole network and then brute-force the overlay (i.e. test all combinations of snowflakes to find complementary ones and recover the IP packets, operation that follow a power-law of the number of snowflakes!). Even if this was feasible, the attacker would still end up with anonymous IP packets and would have to inspect each packet content to find deanonymization hints.
architecture & main principles
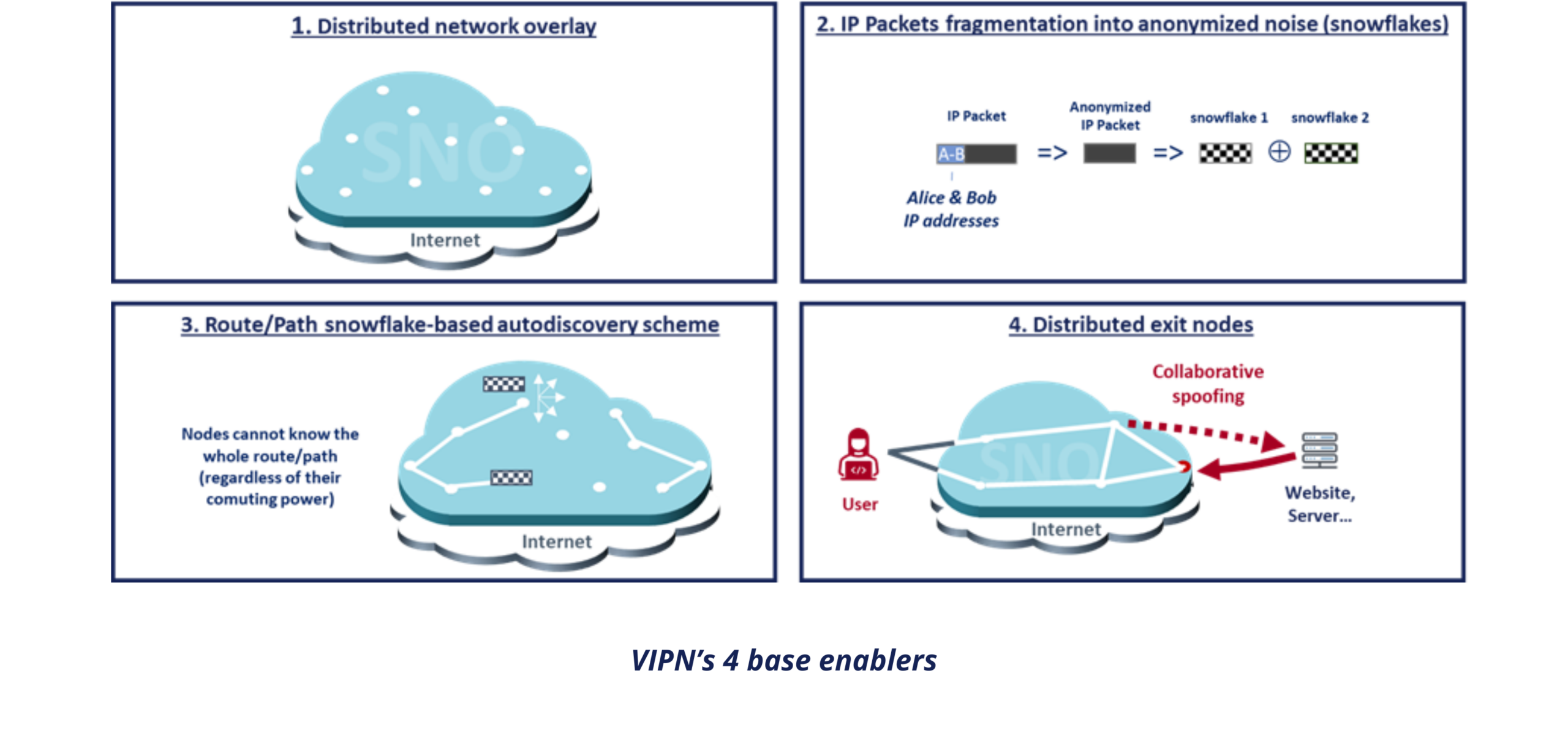
VIPN is based on the combination of 4 complementary enablers:
- An architecture based on a distributed network overlay (SNO) operated by Snowpack, partners, and some clients to which you access with a connector installed on your device or gateway;
- The fragmentation of anonymized IP packets into “snowflakes” through a secret-sharing mechanism (currently the XOR logic operator) for both route creation and data transfer;
- A “snowflake” based auto-discovery mechanism that guarantees anonymous routes’ creation for both ‘Privacy” and “Tunnel” mode;
- Exit node distribution through collaborative spoofing between two SNO nodes selected by the user, to prevent any MITM attacks on “Privacy” and “Tunnel” mode route creation.
These main protocol principles are described in the foundational patent, as well as in our whitepaper (together with its threat model). They have also been popularized in France on cybersecurity specialized podcasts(e.g. OSSIR, NoLimitSecu) and during the 2025 C&ESAR conference.
key Properties
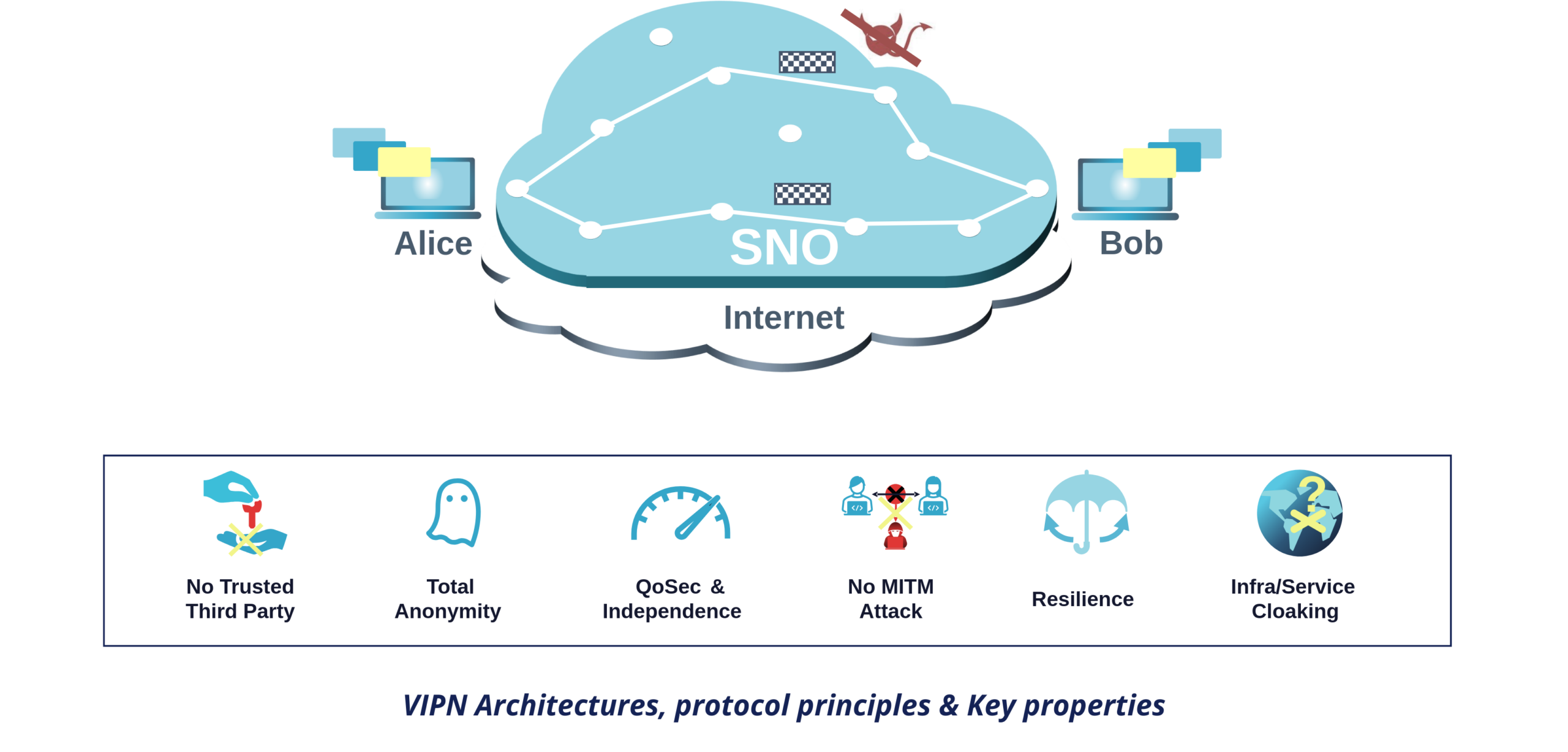
Because VIPN does not rely only on standard TLS encryption between nodes but also on snowflakes and because these snowflakes are transmitted via anonymously built routes: users do not have to trust nodes! Indeed, regardless of their computing power capacity, no node is able to know the origin, destination, and content of a snowflake as they never see these elements (not even in cypher text!).
This approach offers complementary properties:
- Resilience: Nodes are hosted on multiple cloud and hosting providers and operated by various partners;
- No Trusted Third Party and True Anonymity: Neither Snowpack nor any of its partners or customers can identify a route. Therefore they cannot break the anonymity and invisibility of the communications;
- Quality of Security (QoSec): By design, users’ traffics cannot be distinguished because even metadata is cloaked into snowflakes. Attacking communications on SNO therefore requires brute-forcing the entire network overlay. Initial steps imply deploying probes across all SNO nodes (or between nodes), and recording the whole network to retrieve all snowflakes. This latter step is in practice impossible even for a nation-state. Yet, if it were possible, the attacker would then have to test all possible combinations of snowflakes bearing in mind that such operation requires a computing power that grows according to a power-law of the number of snowflakes. This computing power can be estimated thanks to data provided by SNO and be controlled with “snow cannons” injecting additional snowflakes (generated naturally by free users’ traffic, or artificially by Snowpack);
- Immunity to MITM Attacks: By design, man-in-the-middle attack which are at the core of all network attacks are impossible;
- Attack Surface Cloaking: thanks to a Tor-inspired architecture modified to cope with our protocols, VIPN-enhanced servers can be accessed without knowledge of their IP addresses and without any trusted third party, and can operate without any open listening port.
the 2 present VIPN modes
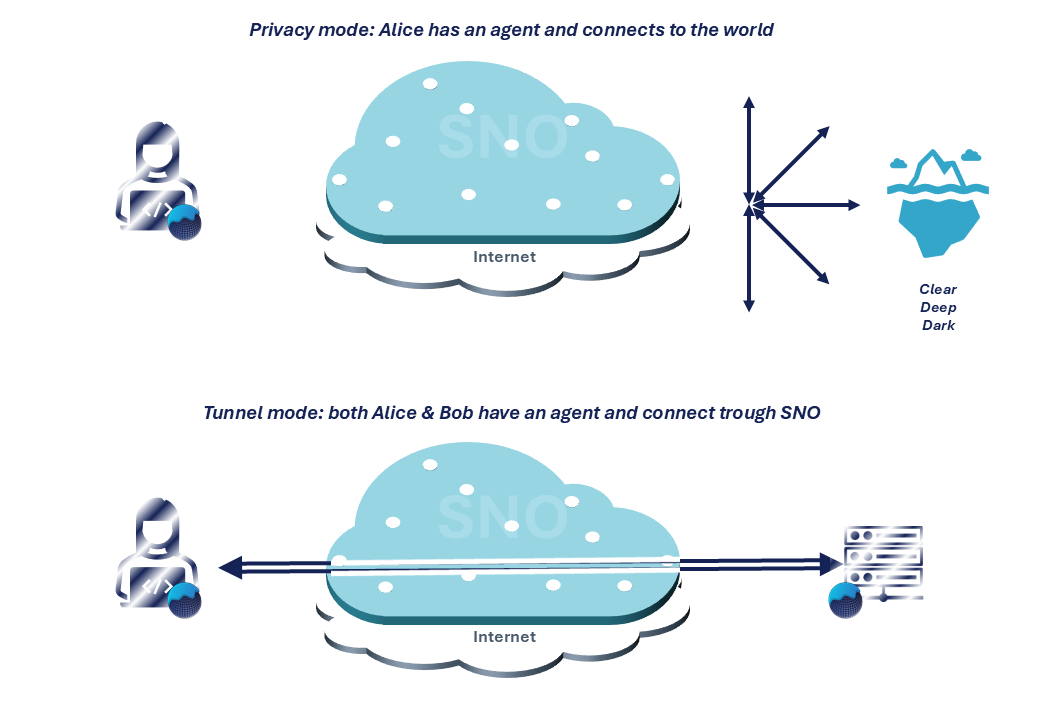
Like Tor (access to clearnet and to Onion services) and VPN (consumer VPN or site-to-site VPN), VIPN has two operating modes:
- “Privacy” or non-collaborative mode, looks like a proxy or consumer VPN services. In this mode, only Alice requires a VIPN agent. This agent cloaks Alice identity through SNO, ensuring a disposable entry point into the Clear, Deep, and Darknet (for access to .onion sites, she can seamlessly integrate it with Tor);
- “Tunnel” or collaborative mode, which resembles a site-to-site or remote access VPN connection. Both Alice and Bob have a VIPN agent to build a route on SNO. In practice, the creation of a tunnel is inspired by Onion services architecture and uses the “Privacy” mode to guarantee its unique properties.
paper